Worried your small business might be the next victim of a cyberattack? You’re not alone; according to TechAisle, 68% of SMBs feel inadequately protected, and losses per security incident have spiked dramatically, averaging $1.6 million in 2024.
Traditional protections, such as firewalls, no longer suffice in today’s environment, leaving your sensitive data vulnerable to costly data breaches. You need a practical, robust solution tailored to the realities of SMBs: Zero Trust security.
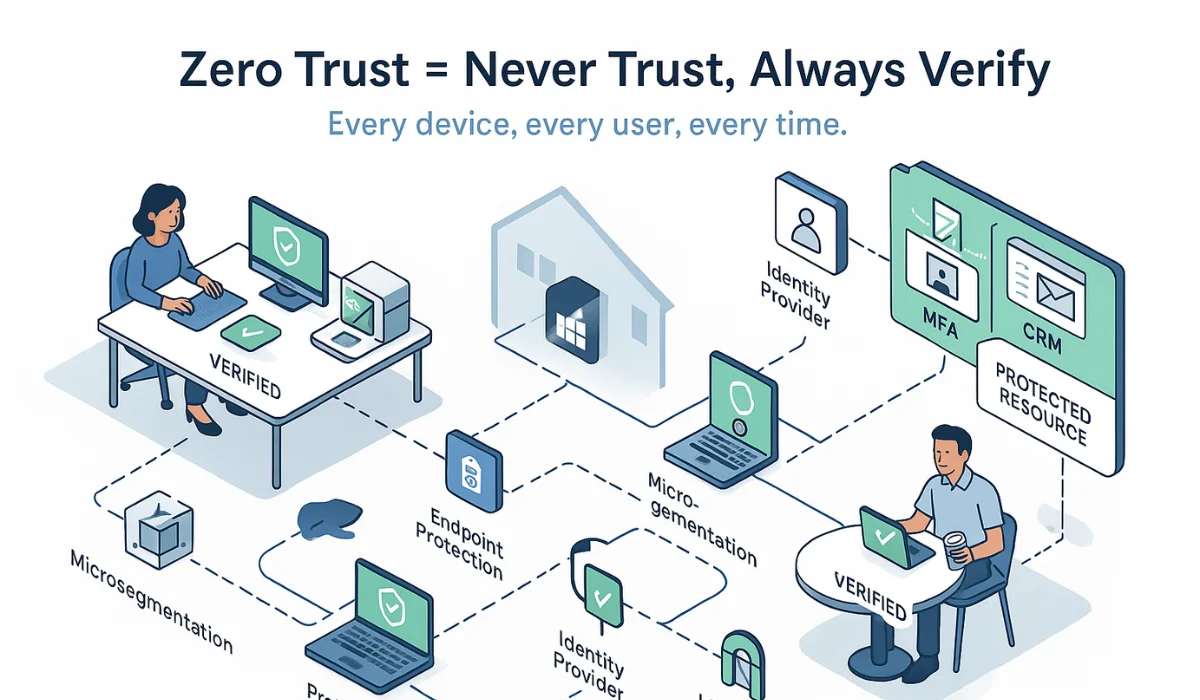
Zero Trust follows the principle of ‘never trust, always verify’; it verifies every user, device, and access request each time. It emphasizes least privilege access, dramatically reduces risks, and harnesses innovations like artificial intelligence to identify threats quickly.
Agencies like CISA recommend adopting this security approach to safeguard your business from evolving cyber threats. By reading this guide, you’ll discover precisely how Zero Trust can strengthen your cybersecurity without complexity.
Key takeaways
- Don’t wait for a data breach to prioritize security. Implementing Zero Trust architecture early helps you contain phishing threats and lateral movement before they become business-ending events.
- You don’t need a massive IT department to secure your business like a Fortune 500 company. With the innovative use of tools like Microsoft Defender and identity-based controls, SMBs can roll out Zero Trust in stages without blowing their budget.
- Trusted networks are no longer enough. In a hybrid work world, Zero Trust flips the script by validating every request, every time, even from internal users or familiar apps.
- Phishing isn’t just about awareness; it’s about access. Zero Trust architecture limits the damage a single clicked link can do by enforcing least privilege access at every layer.
- Most SMBs overestimate how complex Zero Trust is. With focused policies, scalable tech stacks, and help from providers who understand small business needs, you can make enterprise-grade security a practical reality.
What is Zero Trust security?
If you’re relying on traditional security models that trust users once they’re inside the network, you’re leaving the door open to modern cyber threats. Zero Trust security flips that model. It’s built around one simple truth: trust no one and verify everything. Whether it’s a user, device, or app, every access request is treated as potentially risky until proven otherwise.
The Zero Trust security model is based on three essential principles:
- Verify every access request: Confirm user identity and device posture every time someone tries to connect to your systems or sensitive data.
- Enforce least privilege access: Grant users only the minimum permissions required to perform their job, thereby reducing the likelihood of unauthorized access.
- Assume breach: Assume breaches will occur, so ensure your systems are always prepared to detect and contain threats promptly.
To put Zero Trust into action, you’ll use technologies and practices like:
- Identity and Access Management (IAM): Utilize secure authentication methods, such as Multi-Factor Authentication (MFA) and Single Sign-On (SSO), to enhance security.
- Device security checks: Make sure every device meets strict security standards before granting access.
- Network segmentation and microsegmentation: Prevent attackers from moving freely by dividing your network into smaller, isolated zones.
- Continuous monitoring: Maintain a constant watch over network activity in real-time, enabling you to detect and respond to potential threats promptly.
Zero Trust has shifted from an enterprise luxury to an SMB necessity. However, today, it’s an innovative, scalable solution that small businesses can utilize to safeguard their sensitive data, mitigate vulnerabilities, and establish a stronger security posture without overwhelming their internal teams.
Why Zero Trust matters for small businesses
Small businesses are increasingly in the crosshairs of cybercriminals. According to a 2024 Microsoft Security report, one in three SMBs suffered a cyberattack in the past year, with average losses nearing $255,000 and some incidents reaching as high as $7 million.
These attacks aren’t just frequent; they’re financially devastating.
Why are SMBs increasingly vulnerable?
- Remote work and cloud-based tools have expanded the attack surface.
- Bring Your Own Device (BYOD) policies introduce unmanaged endpoints.
- Limited internal security expertise makes it more challenging to detect and contain threats.
- False confidence leads to gaps: Many SMB leaders still believe they’re too small to be targeted or safe because they haven’t been hit yet.
Cybercriminals are aware that small businesses often lack the same defenses as larger organizations. That’s why Zero Trust security isn’t just a best practice; it’s a business imperative.
Here’s where Zero Trust shines:
- Automated, intelligent protection: With Zero Trust, security measures can be automated and enforced without the need for a large IT team.
- Built-in compliance: The framework supports industry regulations like HIPAA (Health Insurance Portability and Accountability Act), PCI (Payment Card Industry Data Security Standard), and CMMC (Cybersecurity Maturity Model Certification), helping you stay audit-ready.
- Flexibility and scalability: Zero Trust adapts as your business grows and evolves in tandem with your IT infrastructure.
By adopting Zero Trust, you’re taking a proactive step to protect your business, your customers, and your future.
How SMBs can implement Zero Trust in practice
You don’t need a whole IT department to start securing your business with Zero Trust. You just need a practical roadmap and the right partners. Here’s how to get started:
1. Strengthen identity and access controls
Begin by securing the front door. Use Multi-Factor Authentication (MFA) and Single Sign-On (SSO) to verify user identity and simplify secure access. According to the Cyber Readiness Institute, MFA can reduce the risk of compromise by up to 99.2%.
2. Segment and Monitor Your Network
Break your network into smaller, secure zones using microsegmentation. This approach keeps sensitive systems isolated, even if one part is compromised, and stops attackers from moving laterally across your environment.
Pair segmentation with continuous monitoring of network traffic, user activity, and access requests. Real-time visibility enables faster threat detection, strengthens your compliance posture, and helps you respond to minor issues before they become major breaches.
3. Secure your endpoints
Protect every access point by deploying Endpoint Detection and Response (EDR) tools, automating patch management, and enforcing device security policies. Even one unprotected device can compromise your entire network.
4. Control vendor and third-party access
Clearly define and enforce access policies for all third-party service providers to ensure compliance and security. Ensure their permissions are limited to what is strictly necessary, and revoke access when it’s no longer needed.
5. Get expert guidance
Zero Trust doesn’t have to be complex. A trusted partner like Keystone Technology Consultants can guide your rollout, tailoring every step to your needs and helping you avoid common pitfalls.
Keystone makes Zero Trust easy for small businesses, eliminating the need for a large IT team. By following this path, you’re building a cybersecurity foundation that will grow with your company and shield you from emerging threats.
Why SMBs choose Keystone Technology Consultants for Zero Trust
By embracing Zero Trust security, you take a proactive stance against today’s most sophisticated cyber threats. This guide outlines the core principles, including least privilege access and continuous verification, and provides practical steps to help your small business establish a stronger, more resilient security posture.
Zero Trust not only safeguards your sensitive data from breaches but also ensures your business remains compliant and resilient in an evolving digital landscape.
At Keystone Technology Consultants, we understand the unique cybersecurity challenges that SMBs face. With over 25 years of experience, we’re committed to simplifying and streamlining your path to effective Zero Trust implementation.
If you’re ready to fortify your business against cyber threats without complexity, we invite you to take the next step.
Schedule your complimentary Zero Trust readiness consultation today, and let’s start securing your business’s future together.
FAQs
Is Zero Trust Security Too Advanced for Small Businesses?
Zero Trust is modular and scalable, meaning SMBs can adopt it gradually. You don’t need a large IT team; start with high-impact areas, such as identity management, and grow from there.
How long does it take to implement Zero Trust?
Many SMBs can begin their Zero Trust journey in just a few weeks. A phased approach helps you secure high-risk areas early while minimizing business disruption.
Does Zero Trust support compliance with regulations like HIPAA or PCI?
Yes. Zero Trust helps meet HIPAA, PCI, and CMMC requirements by enforcing least privilege access and monitoring activity. This makes audits easier and reduces the risk of violations.