Nonprofits are now prime targets for cybercriminals. With access to sensitive donor and financial information, they face growing risks once reserved for large corporations.
InfoSecurity Magazine reports a 35.2% spike in email-based attacks on nonprofits last year. These attacks, from phishing scams to ransomware and full-blown data breaches, threaten your organization’s finances, reputation, and mission.
Cyberattacks are becoming more common. Let’s explore why you’re targeted, review common threats, and uncover actionable strategies for your nonprofit to stay protected.
Key Takeaways
- Protect sensitive donor and financial data with MFA and encryption.
- Cut risks by regularly training staff and volunteers with security awareness and phishing drills.
- Uncover weaknesses early with routine risk assessments, audits, and penetration tests.
- Stay ready with a clear, documented incident response plan.
- Boost security without overextending resources by leveraging modern cybersecurity tools and services.
Why Nonprofits Are Prime Targets for Cybercriminals
Your nonprofit handles sensitive data, from donor lists to financial records, that cybercriminals see as a valuable target. High-profile breaches, like the incident at Broward Health, highlight the risk of losing this trust. Meanwhile, tight budgets make investing in robust security measures difficult, leaving many nonprofits particularly vulnerable.
Reliance on Volunteers and External Partners
Nonprofits rely on volunteers and vendors, but these partners often lack cybersecurity training. While dedicated volunteers may not have undergone comprehensive cybersecurity training, they are more susceptible to phishing scams and social engineering tactics.
Similarly, external partners might not follow rigorous cybersecurity standards necessary to protect your organization’s data, introducing vulnerabilities through third-party access.
Common Cybersecurity Threats Facing Nonprofits

Understanding the threats targeting nonprofits is essential for a robust cybersecurity plan. Here are the primary cyberattacks you should know about:
Phishing Attacks
Phishing remains the number one threat. Cybercriminals send fake emails that mimic trusted sources, tricking recipients into clicking malicious links or revealing sensitive information. A single click can lead to credential theft, data breaches, and financial fraud.
Ransomware
Ransomware attacks encrypt your critical data and hold it hostage until a ransom is paid. For nonprofits with limited budgets, the cost of recovery in funds and operational downtime can be devastating.
Social Engineering Tactics
Cybercriminals use social engineering to manipulate employees into divulging confidential information. Attackers exploit human psychology by impersonating donors, partners, or trusted colleagues, making these tactics hard to defend against without proper training.
Data Breaches
Data breaches often occur from weak security measures, exposing sensitive donor and beneficiary information. The resulting fallout can include significant financial losses, severe reputational damage, and legal or regulatory challenges that further strain your resources.
Vulnerabilities in Nonprofit Organizations
Nonprofits face unique cybersecurity challenges due to limited resources, outdated systems, and heavy reliance on human effort. The human factor is often the weakest link; employees and volunteers may lack awareness of cybersecurity best practices, making them prime targets for phishing scams.
Additionally, using personal or unsecured devices and outdated software and protocols creates further entry points for attackers. Reliance on external vendors also introduces risk if these third parties do not uphold strict security standards.
Effective Cybersecurity Strategies for Nonprofits
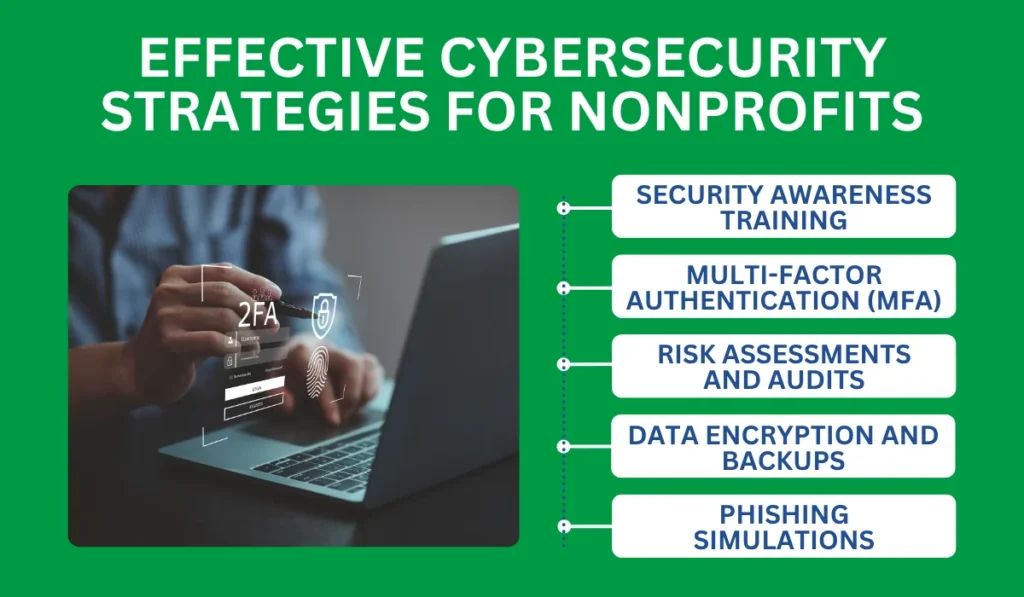
Now that you understand the key threats and vulnerabilities, it’s time to turn the tide. Here are actionable strategies to safeguard your organization:
Security Awareness Training
Regular training empowers your team to recognize phishing attacks and social engineering tactics. Periodic workshops and phishing simulations help keep everyone vigilant.
Multi-Factor Authentication (MFA)
Implement MFA for all user accounts, especially those handling sensitive data. This extra verification step significantly reduces the risk of unauthorized access if credentials are compromised.
Risk Assessments and Audits
Conduct regular cybersecurity audits and penetration tests to pinpoint vulnerabilities before cybercriminals exploit them. These assessments provide invaluable insights to strengthen your IT infrastructure.
Data Encryption and Backups
Encrypt sensitive data in transit and at rest, rendering it useless to unauthorized users. Maintain regular offline backups to ensure a swift recovery in case of a data breach or ransomware attack.
Phishing Simulations
Periodically test your employees with phishing simulations to assess their ability to spot and report suspicious emails, reinforcing training and identifying further education needs.
Leveraging Cybersecurity Services and Tools
Beyond internal measures, leveraging specialized cybersecurity services can further fortify your organization’s defenses.
Cloud-Based Security Solutions
Consider partnering with cloud service providers that offer robust, built-in security functionalities. For example, Microsoft’s security tools can provide enhanced protection through features like advanced threat detection, real-time monitoring, and automated patch management. Cloud-based solutions enhance security and offer scalability as your organization grows.
Firewalls and Endpoint Protection
Implement powerful firewalls and endpoint protection software to shield your systems from malware and cyberattacks. Firewalls act as the first line of defense, filtering out suspicious traffic and preventing unauthorized access. Endpoint protection ensures that every device connected to your network is secure and monitored continuously.
Incident Response Plans
Have a clear, documented incident response plan ready before an attack hits. This plan should include clear communication protocols, designated roles, and recovery procedures. Knowing exactly what to do when an incident occurs can mitigate damage and reduce downtime, ensuring your organization can quickly return to its mission.
Building a Resilient Security Posture
Creating a resilient cybersecurity framework is a long-term commitment involving technology, people, and processes.
Certifications and Compliance Standards
Adhering to recognized cybersecurity standards and certifications, such as GDPR or HIPAA, where applicable, helps protect sensitive data and enhances your organization’s credibility. By regularly reviewing and updating your security protocols, you ensure that your practices meet the latest regulatory requirements.
Engaging Stakeholders in Cybersecurity Efforts
Cybersecurity isn’t just IT’s job, it’s everyone’s responsibility. Inform your board members, donors, and volunteers about the risks and measures you are taking to engage them in your cybersecurity initiatives. When all stakeholders understand their role in maintaining a secure environment, collective vigilance significantly reduces the overall risk.
Strengthen Your Cybersecurity Posture Today
In an era of relentless cyberattacks, from phishing scams to ransomware, complacency is not an option. Your nonprofit’s mission, donor trust, and financial stability depend on your ability to defend against these threats. You can build a robust defense around your most valuable assets by implementing proactive measures like regular security training, multi-factor authentication, ongoing risk assessments, and expert cybersecurity partnerships.
You’re here to serve your community, don’t let cybercriminals steal that away. Taking action today strengthens the trust you’ve built with your donors and safeguards your mission.
Reach out today to partner with cybersecurity experts who understand your unique challenges and can help take IT off your plate so you can focus on serving your community.




