Introduction
If you’re responsible for protecting your organization’s information systems, you already know this: cyberattacks aren’t slowing down. They’re growing more sophisticated, more frequent, and more expensive. IBM reports that the average data breach now costs $4.88 million. That kind of exposure isn’t just a budget issue; it’s a business continuity risk.
A well-executed cybersecurity audit is one of the most effective ways to fight back. It gives you a clear, structured view of your information security posture, helps you meet compliance requirements, and uncovers vulnerabilities before threat actors do.
Whether you’re part of a dedicated IT security team or juggling multiple hats as a business leader, this guide will walk you through a complete audit process. You’ll get real-world strategies, a practical checklist, and a sharper understanding of where internal auditors and external partners fit.
Key takeaways
- An audit isn’t about passing. It’s about preparing. Use it to uncover blind spots, validate controls, and improve security before attackers find the cracks.
- Every audit finding needs a name and a date. Without clear ownership and deadlines, even critical issues will sit unresolved.
- Technical risks only matter when mapped to business impact. Translate findings into clear, business-focused language to earn executive support and secure investment.
- Audit fatigue is real, but structure solves it. A repeatable process with a focused checklist reduces chaos and keeps progress on track.
- Your next breach might come from last quarter’s delay. Prioritize timely remediation and schedule follow-ups to prove closure and continuous improvement.
Understanding cybersecurity audits
A cybersecurity audit is a systematic evaluation of your security controls and related processes. Its main goals are to uncover vulnerabilities, measure control effectiveness, and confirm compliance with regulations such as ISO 27001, NIST CSF 2.0, HIPAA, and PCI DSS.
Core Audit Objectives
A cybersecurity audit helps you uncover and address gaps in your security posture. Specifically, it enables your organization to:
- Identify vulnerabilities across policies, technologies, and human behavior.
- Evaluate existing security controls against recognized frameworks and industry best practices.
- Confirm compliance with relevant regulations and contractual obligations.
- Assess and communicate cybersecurity risk to critical assets and services.
- Prioritize remediation efforts and monitor ongoing security improvements.
Types of Cybersecurity Audits
Internal audits
Your team manages internal audits, which are typically conducted quarterly or before external assessments. They’re ideal for identifying issues early and reinforcing a culture of continuous improvement across your cybersecurity program.
External audits
External audits are handled by independent third parties and are performed annually or when mandated by clients or regulators. They provide an objective, outside perspective on your organization’s security posture.
Compliance audits
Compliance audits, triggered by specific legal, regulatory, or contractual requirements, confirm your adherence to frameworks such as HIPAA, PCI DSS, or GDPR. They are essential for demonstrating regulatory alignment.
Technical audits
Run technical audits after major infrastructure changes and examine your security architecture in depth. These audits focus on configuration, patching, and penetration testing to uncover system-level weaknesses.
Key Benefits of a Cybersecurity Audit
A well-executed cybersecurity audit provides a clear path to stronger defenses, smarter risk management, and greater organizational trust. Here are the core benefits:
- Proactively Reduce Risk: Identify and address vulnerabilities before they escalate into costly incidents or compliance violations.
- Strengthen Your Security Posture: Make clear, measurable improvements that can be confidently communicated to executive leadership, board members, and regulatory bodies.
- Build Trust with Customers and Partners: Demonstrate a mature, accountable approach to cybersecurity, enhancing credibility and confidence among clients, vendors, and stakeholders.
The Cybersecurity Audit Process
A cybersecurity audit exposes risk before attackers do. This process gives you a structured, repeatable way to evaluate your security posture, align with frameworks like NIST or ISO, and drive continuous improvement.
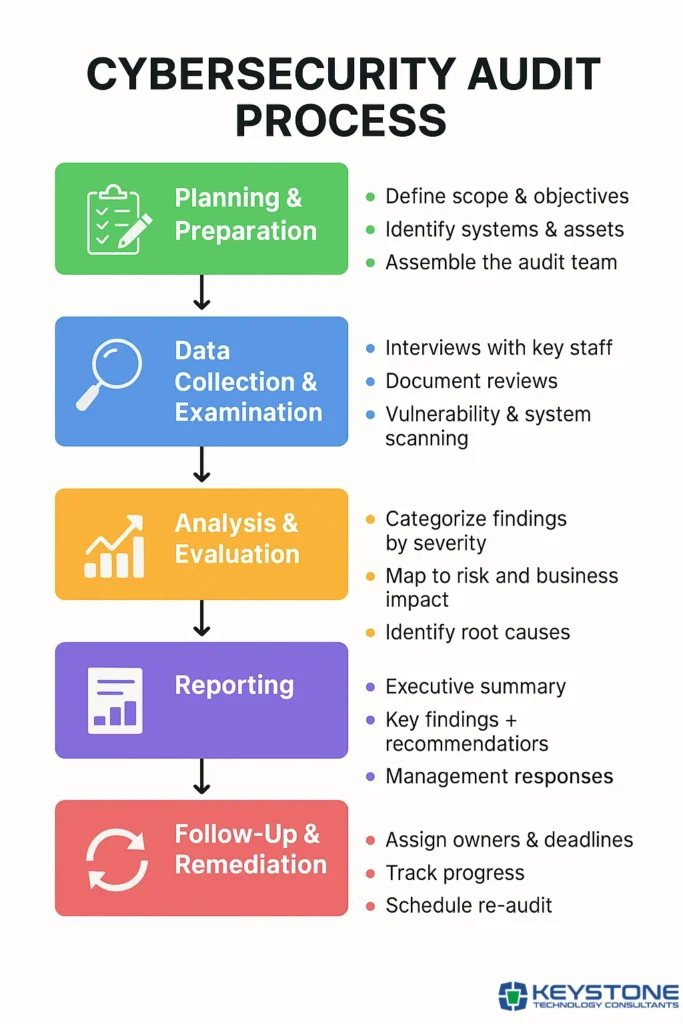
1. Planning & Preparation
Every effective cybersecurity audit begins with a clear and deliberate planning phase. This is where you define the purpose, set boundaries, and ensure everyone involved understands what is being assessed and why. Careful preparation reduces confusion, avoids scope creep, and ensures the audit delivers value aligned with your organization’s risk profile and strategic priorities.
Define the scope, objectives, and methodology
Start by outlining the audit’s scope. This includes the business units, data types, systems, and processes that will be evaluated. Be specific and realistic to ensure the audit remains focused and manageable. Objectives should align with broader organizational goals and risk frameworks such as NIST CSF, ISO/IEC 27005, or COBIT. Establish whether the audit will follow a controls-based, risk-based, or hybrid methodology, and determine the level of depth required.
Identify assets, systems, and processes to include
Once the scope is defined, compile an accurate inventory of the systems, applications, networks, and operational processes included in the audit. This should include physical and virtual assets, cloud environments, and third-party services where applicable. Understanding what is “in scope” ensures the audit team can assess interdependencies, critical functions, and areas of elevated risk.
Gather relevant documentation
Collect all supporting documentation before fieldwork begins. This typically includes cybersecurity policies, system configuration baselines, network diagrams, access control procedures, incident response plans, and results from previous audits or vulnerability assessments. Reviewing these materials in advance helps auditors establish context and evaluate whether existing documentation reflects actual practices.
Establish the audit team
Assemble a team with the right mix of technical, analytical, and organizational expertise. Internal team members offer knowledge of systems and processes, while external auditors bring objectivity, fresh perspective, and regulatory familiarity. Clarify roles and responsibilities early, especially regarding coordination, evidence collection, and stakeholder communication.
Develop a detailed audit plan and schedule
Create a written audit plan that outlines the timeline, audit steps, communication protocols, and any dependencies. Align the audit schedule with business operations to minimize disruption, especially for critical systems. Include milestones for each phase—planning, data collection, analysis, reporting, and remediation planning—to ensure accountability and progress tracking.
A well-prepared audit identifies risk and sets the stage for continuous improvement and stronger decision-making. Even the most detailed technical findings can lose strategic relevance without this foundational step.
2. Data Collection & Examination
This phase is about evidence, not assumptions. The goal is to gather reliable, verifiable data to determine whether your security controls work as intended across people, processes, and technology. A well-rounded audit uses multiple data sources and validation methods to uncover hidden risks, close the gap between policy and reality, and establish a defensible basis for your findings.
To assess control effectiveness, use a combination of techniques:
Interviews
Speak with system owners, IT staff, and business leaders to understand how security practices are implemented daily. Interviews help auditors identify gaps between documented procedures and real-world behaviors and often reveal tribal knowledge or undocumented workarounds that introduce risk.
Tip: Use structured questions and take detailed notes to ensure interview consistency.
Document Review
Examine all relevant documentation, including cybersecurity policies, procedures, incident response plans, network diagrams, asset inventories, and previous audit reports. You’re looking for completeness and alignment with current business practices and compliance requirements.
Ask: Are policies current? Are they communicated? Do employees follow them?
System and Network Scanning
Use automated vulnerability scanners and security tools to identify outdated software, unpatched systems, weak configurations, and exposed services. These scans help surface technical flaws—like open ports, insecure protocols, or known CVEs—that may be invisible during interviews or document reviews.
Note: Prioritize critical assets and systems that handle sensitive data.
Configuration Reviews
Manually or automatically review the settings of servers, endpoints, firewalls, databases, and applications. You’re checking whether these systems are configured according to hardening guidelines (e.g., CIS Benchmarks or vendor best practices) and whether any insecure defaults remain in place.
Focus on: Password policies, access controls, encryption settings, and patch levels.
Log Analysis
Analyze system, application, and security logs to detect signs of past or ongoing incidents, policy violations, or unusual patterns. Look for failed login attempts, unauthorized changes, data exfiltration indicators, and anomalies that suggest a breakdown in monitoring or response processes.
Requirement: Ensure logs are centralized, retained per policy, and protected from tampering.
Direct Observation
Where feasible, observe employees performing sensitive operations, such as onboarding new users, responding to alerts, or accessing restricted systems. This hands-on approach helps validate whether staff follow established procedures or take shortcuts that increase risk.
Example: Does the helpdesk truly verify identity before resetting passwords?
By combining these techniques, you move beyond surface-level compliance and gain a comprehensive view of your actual security posture. Tools can detect misconfigurations—but only observation and analysis can explain why they exist, who they affect, and how to fix them.
3. Analysis & Evaluation
Once you’ve collected the data, turn findings into insight. Map vulnerabilities to risk levels using probability and impact. Categorize issues by severity (low, medium, high)and trace each back to its root cause, whether a process failure, tooling gap, or human error. Summarize the results in business terms so leadership can take informed action.
Tip: Many teams struggle with analysis because alerts pile up faster than people can investigate. The latest ISACA survey found that 66% of cybersecurity professionals report higher stress than five years ago, driven by escalating threats.
Reporting and follow-up
An audit’s value isn’t in the findings; it’s in what happens next. Your report should translate technical issues into business priorities, and your follow-up plan should drive measurable change. Here’s how to close the loop with impact.
4. Clear, Actionable Reporting
Your audit report should be brief, structured, and aligned with your audience. Include:
- Executive Summary – A one-page, plain-language overview of risks and priorities.
- Scope & Methodology – What you assessed, why it matters, and how you did it.
- Findings – Grouped by severity, mapped to relevant standards or frameworks.
- Risk Assessment – Focused on business impact, not just technical detail.
- Recommendations – Prioritized fixes with estimated effort and cost.
- Management Response – Documented agreements, exceptions, and timelines.
Deliver the report to security leaders, system owners, and compliance teams to ensure cross-functional alignment.
5. Follow-Up & Remediation
Reporting isn’t the finish line; remediation is. Assign clear owners and deadlines for every finding. Use a GRC tool or dashboard to track progress and surface blockers. Implement continuous monitoring to verify that controls remain effective over time. And don’t forget the final step: schedule a follow-up audit to validate closure and demonstrate improvement.
This isn’t just best practice; it’s a recognized gap. McKinsey’s 2025 Global GRC Benchmarking Survey found that most organizations acknowledge a “need for improvement” in oversight, remediation, and technology enablement. This underscores the growing urgency for structured, integrated follow-up processes that move beyond one-time fixes to sustained risk reduction.
How the Audit Process Aligns with Compliance Frameworks
A cybersecurity audit isn’t just an internal best practice; it’s a foundational part of meeting external compliance standards. Frameworks like NIST CSF 2.0 and ISO/IEC 27001 provide structure and accountability, but mapping your audit process to them ensures your team is building a program that’s both secure and certifiable.
The matrix below shows how each audit phase aligns with key domains from these two leading standards, helping you translate tactical actions into strategic outcomes and regulatory readiness.
| Audit Phase | NIST CSF 2.0 | ISO/IEC 27001 (2022) |
|---|---|---|
| 1. Planning & Preparation | Identify (ID.GV, ID.AM) | Clause 4 (Context), Clause 5 (Leadership), A.5 (Policies), A.6 (Roles) |
| 2. Data Collection & Examination | Protect (PR.AC, PR.IP), Detect (DE.CM) | A.7 (HR Security), A.8 (Asset Management), A.12 (Operations), A.13 (Communications) |
| 3. Analysis & Evaluation | Identify, Protect, Detect | A.9 (Access Control), A.14 (System Acquisition), A.15 (Supplier Relationships), A.17 (Monitoring) |
| 4. Reporting | Identify (ID.RA), Respond (RS.MI, RS.CO) | A.16 (Incident Management), A.18 (Compliance), Clause 9 (Performance Evaluation) |
| 5. Follow-Up & Remediation | Recover (RC.IM), Respond (RS.IM), Protect (PR.IP) | Clause 10 (Improvement), A.10 (Cryptography), A.11 (Physical Security), A.18 (Continuous Improvement) |
8 Critical Areas to Include in Your Cybersecurity Audit
These eight domains represent the highest-risk, highest-impact areas for most organizations. Prioritize them to uncover critical gaps and prove real-world security maturity.
Risk Management
Are you actively cataloging threats and rating them by likelihood and impact? An updated risk register is the foundation of every meaningful security decision.
Access Control
Audit how access is granted, reviewed, and revoked. Enforce least privilege, require multi-factor authentication, and close orphaned accounts quickly.
Network Security
Review segmentation, firewall rules, and IDS/IPS alerts. Look for excessive permissions, stale rules, and signs of unauthorized lateral movement.
Data Protection
Ensure sensitive data is encrypted both in transit and at rest. Validate backup integrity and confirm that data handling policies are consistently applied.
Endpoint Security
Check that all devices, servers, laptops, and mobile endpoints run updated Endpoint Detection and Response (EDR) and antivirus software. Verify timely patching and secure configurations.
Incident Response
Evaluate your incident response plan: is it tested, current, and clear? Tabletop exercises and response logs offer insight into real-world readiness.
Business Continuity
Validate that off-site backups exist and that recovery objectives, Recovery Point Objective (RPO), and Recovery Time Objective (RTO) are aligned with business requirements. Regularly test backup restorations to ensure they function as expected and to avoid unexpected failures during a real-world disaster.
Compliance
Map your audit findings to applicable standards like HIPAA, PCI DSS, and GDPR. Demonstrate not just technical safeguards, but regulatory alignment.
Conclusion
A cybersecurity audit isn’t just a box to check. It’s a key part of your security strategy against costly cyberattacks, data breaches, and compliance failures. By following a structured process, focusing on what matters, and using the right tools, you can turn audits into a powerful strategy for protecting sensitive information, strengthening IT security, and proving your value to stakeholders.
If you’re ready to move from findings to fixes and want to streamline your process, our downloadable checklist can help.
At Keystone, we don’t just point out risks, we help you solve them. If you’re ready to eliminate blind spots, reduce audit fatigue, and build a security program your board can trust, let’s talk today.
Need help turning audit results into real-world improvements? Let’s talk about building a security program your team and board can trust.




