You manage firewalls, patch systems, and educate users, but sensitive data still finds ways to slip through. That’s the reality for today’s IT and security leaders. The threats aren’t theoretical, whether you’re securing a healthcare network, financial systems, or SaaS infrastructure. They’re already inside, moving fast, and exploiting every gap in your architecture.
Microsoft warns that data breaches aren’t just possible, they’re inevitable. The real question isn’t if your sensitive data will be targeted, but when it will escape unless you’re prepared to stop it.
Malware, phishing, misconfigurations, and ransomware target data in use, in transit, and at rest, well beyond your endpoints. Without visibility into how personally identifiable information (PII) and intellectual property move across your network, you’re operating with blind spots.
That’s where network data loss prevention helps you take control.
More than just a firewall or antivirus layer, modern data loss prevention solutions are built to understand the functions of sensitive data, identify risky use cases, stop data leaks, and secure data access before it’s too late. These tools help you spot and stop threats, whether they come from outside attackers or insiders.
In this guide, you’ll learn how network DLP fits into your larger cybersecurity and data security strategy, what it looks like in practice, and how Keystone can help you implement scalable, enterprise-ready security solutions that close the gaps others miss.
Key takeaways
- DLP isn’t just for compliance; it’s your frontline for stopping data exposure. When used proactively, network DLP delivers real-time insight into risky data behaviors long before they become breaches.
- Most data leaks don’t come from hackers; they come from your systems and users. Misconfigurations, shadow IT, and insider misuse bypass traditional defenses unless network DLP is watching.
- If you haven’t mapped your data flows, you’re flying blind. Use DLP discovery to uncover where sensitive data lives and moves, especially across apps and channels you didn’t authorize.
- Jumping straight to blocking is a recipe for chaos. Start in monitor-only mode to baseline normal behavior, reduce false positives, and earn trust before flipping the enforcement switch.
- DLP works best when it is integrated with other tools. Integrate it with your SIEM, IAM, and Zero Trust tools to turn scattered defenses into an intelligent, adaptive security fabric.
1. Understanding data loss and its impact
Data loss occurs whenever sensitive information, from credit card numbers to design blueprints, leaves your control. That escape can be intentional (data exfiltration by an attacker or insider) or accidental (data leakage through mis-sent emails). Common channels include:
- Email and instant messaging
- Web traffic (HTTP/HTTPS) and cloud applications
- File-transfer protocols (FTP, SFTP)
- Shadow IT services you never approved
The consequences are costly and long-lasting. Victims face regulatory fines, legal fees, and reputational damage long after cleanup. The Identity Theft Resource Center reports that 70% of 2024 breach notices omitted critical details about how attackers got in, up from 58% the prior year, making incident response even more challenging. Meanwhile, more than 1.7 billion individuals had personal data compromised in 2024, a staggering 312% year-over-year surge.
2. What is network data loss prevention?
Network DLP is a set of security controls that detect, monitor, and stop sensitive data from leaving your organization’s network. Unlike endpoint-only or cloud-only products, network DLP focuses on data in motion, packets traversing routers, switches, VPN concentrators, and proxy servers.
Core Functions of Network DLP
Network DLP operates through four primary functions, each designed to reduce the risk of sensitive data exposure:
1. Discovery
Network DLP begins by scanning network traffic and connected repositories for sensitive data types, such as personally identifiable information (PII), protected health information (PHI), PCI DSS-regulated data, and intellectual property. This step builds a complete inventory of critical data across your organization, ensuring that nothing slips through the cracks.
2. Monitoring
Once discovery is complete, monitoring kicks in. Network DLP uses techniques like Deep Packet Inspection (DPI), keyword pattern recognition, regular expressions, data fingerprinting, and machine learning to analyze real-time traffic. This allows the system to flag any content that matches DLP policies or violates regulatory thresholds.
3. Blocking
Network DLP enforces security policies directly within network traffic flow to prevent data loss. Inline appliances and proxy-based solutions can block unauthorized transfers before data leaves your environment. This real-time enforcement helps stop data exfiltration, whether intentional or accidental.
4. Alerting and Reporting
Finally, network DLP tools generate detailed alerts and reports based on contextual information, such as the user, application, and destination of the flagged data. These insights integrate with Security Information and Event Management (SIEM) platforms, accelerating your team’s incident response and simplifying audit preparation for regulatory compliance.
Because analysis happens inline, you can apply contextual controls. For example, you can allow encrypted financial reports to your ERP portal but block the same file heading from a personal Gmail account.
3. Benefits of implementing network DLP
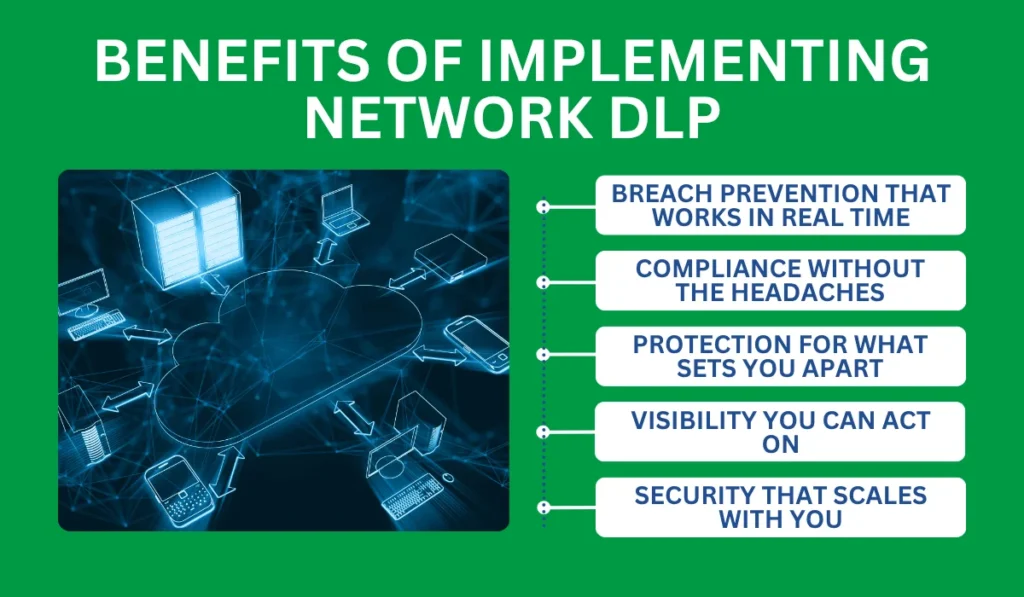
Network data loss prevention doesn’t just detect threats, it reshapes how you secure, control, and capitalize on your most valuable data.
Breach Prevention That Works in Real Time
Network DLP stops sensitive data from slipping out through malicious exfiltration or careless mistakes. It detects and blocks unsanctioned transfers before damage is done. With data theft driving 94% of cyberattacks, this is a necessity.
Compliance Without the Headaches
Staying compliant with regulations like GDPR, HIPAA, and PCI DSS is easier when DLP does the heavy lifting. Automated enforcement, audit-ready logs, and real-time policy controls help you meet requirements without slowing down your operations.
Protection for What Sets You Apart
Your intellectual property is the heartbeat of your business. Network DLP keeps proprietary code, designs, and confidential strategies from walking out the door, intentionally or not.
Visibility You Can Act On
DLP lets you see every movement of sensitive data, who’s sending it, where it’s going, and how it’s being used. That insight helps you shut down risk before it spirals.
Security That Scales With You
By integrating with SIEM, zero trust frameworks, and incident response tools, network DLP strengthens your entire security stack. It’s the connective tissue that turns reactive defense into proactive control.
4. Key components of a network DLP system
An effective network DLP system is more than a single tool. It’s a coordinated set of technologies that monitors, controls, and protects sensitive data across your entire infrastructure.
It starts with network DLP appliances, physical or virtual sensors placed directly in the path of network traffic or connected through SPAN or TAP. These appliances inspect packets in real time without interrupting network performance.
The management console is your centralized command center. From this interface, security teams can create policies, fine-tune detection logic, investigate flagged incidents, and generate reports that support compliance and auditing efforts.
At the core is the policy engine, which evaluates traffic using techniques like regex, data fingerprinting, and exact data matching. It considers context such as user identity, role, and destination to determine whether to allow, block, or quarantine the data.
Repository connectors scan local file shares and cloud storage platforms to locate and secure data at rest. This ensures that sensitive data doesn’t sit unprotected in forgotten or unsanctioned locations.
Finally, endpoint agents can be installed on employee devices to extend protection beyond the network. These agents provide visibility into data use on laptops and remote endpoints, aligning endpoint activity with your broader DLP strategy.
These components deliver complete coverage, helping you secure data wherever it moves or resides.
5. How to Implement Network DLP
Rolling out network data loss prevention requires more than just installing tools. It’s a strategic process that demands alignment with your business objectives, regulatory environment, and existing infrastructure. These best practices will help you build a foundation that scales, adapts, and protects over time.
Identify and Classify Sensitive Data
Start by locating and labeling the data that matters most. Automated classification tools tag intellectual property, personally identifiable information (PII), and confidential business documents. This critical first step ensures your DLP controls are aligned with actual business risk and not just theoretical coverage.
Define Clear and Enforceable DLP Policies
Work closely with legal, compliance, and data governance teams to define what constitutes sensitive data and how it should be handled. Once those definitions are clear, translate them into enforceable, machine-readable rules that drive detection and enforcement across your network.
Choose the Right DLP Technology for Your Environment
Select solutions that fit your current and future needs. Consider performance throughput, real-time inspection capabilities, cloud readiness, and integration support for tools like SIEM and firewalls. Evaluate the trade-offs between on-premises sensors and SaaS-based DLP offerings to ensure your architecture stays flexible.
Roll Out in Phases to Build Confidence and Accuracy
Begin deployment in a monitor-only mode to establish a baseline for normal data behavior. Use this observation period to reduce false positives, tune policy thresholds, and refine detection logic. Once your system is stable and your team is confident, shift to active blocking mode to prevent real-time data loss.
Empower Your Users Through Training
Your DLP strategy is only as strong as the people using your systems. Equip employees with training that helps them recognize phishing attempts, handle sensitive data responsibly, and report suspicious behavior. Turning users into informed allies reduces the risk of accidental violations.
Monitor, Audit, and Remediate Continuously
Treat DLP as a living system. Review your policies and detection rules regularly, analyze alerts for signs of emerging risks, and route critical incidents into your broader security workflows. The more frequently you tune and test, the more effective your defenses will become.
Integrate DLP with Your Broader Security Ecosystem
Your DLP system should operate as part of a unified security architecture for maximum protection. Connect it with identity and access management (IAM), SIEM platforms, and zero trust segmentation. This integration enables layered defenses that can respond dynamically to real-world threats.
6. How Keystone helps you succeed
Protecting sensitive data isn’t just a compliance checkbox. It’s a continuous battle against evolving threats, limited resources, and complex infrastructure. Keystone helps you stay ahead by removing the guesswork and giving your security team clarity, control, and capacity.
What our experts deliver
- Custom-fit network DLP solutions: We evaluate your architecture and choose the right-fit DLP systems, on-prem, cloud DLP, or hybrid, to match your business and compliance needs.
- End-to-end deployment: From initial design to policy development, pilot testing, and full-scale rollout, we handle implementation so your team doesn’t have to.
- Around-the-clock monitoring and response: Keystone’s security operations center monitors and responds around the clock with real-time alerts, security incident triage, and expert remediation, even when your team is offline.
- Compliance support you can rely on: Whether you’re navigating GDPR, HIPAA, or PCI DSS, we align policies and reporting to meet evolving standards and auditor expectations.
- Seamless integrations: We connect DLP data to your SIEM, CASB, and endpoint tools, giving your security teams full visibility across every layer.
- Integrated encryption and permissions settings: We help enforce encryption and permissions policies to protect data in motion, at rest, and in use, reducing your risk of exposure.
Why leading teams choose Keystone
When protecting sensitive data is mission-critical, security leaders turn to Keystone for expertise, clarity, and results. Our clients gain a partner committed to long-term protection and measurable impact.
Deep Expertise in Data Security and Risk Mitigation
Our team has years of experience in data protection, network defense, and compliance strategy. We understand the evolving threat landscape and tailor every solution to address real-world vulnerabilities, not just theoretical risks.
A Proactive, Strategic Approach to Security
We don’t wait for threats to make headlines. Keystone builds forward-looking security strategies that reduce unauthorized access, minimize attack surfaces, and strengthen your overall security posture from day one.
Results That Make a Measurable Difference
Clients who implement our network DLP solutions see a clear reduction in costly incidents, from regulatory fines and lawsuits to data breaches and operational downtime. We aim to lower your risk while helping your team operate more confidently.
Your Data Deserves More Than Just Protection
Your data is one of your organization’s most valuable assets. At Keystone, we treat it that way. Our job is to help you protect your value, integrity, and role in driving your business forward.
Ready to protect what matters most?
You don’t need another tool; you need a partner. Keystone gives you more than just software. We help you build a plan, stay supported, and stay on track, starting day one.
Whether you’re building your first data loss prevention strategy or scaling enterprise-wide protections, we’re here to help you move faster, reduce risk, and prevent the next security incident before it happens.
Book a free consultation to explore how a custom-fit DLP strategy can strengthen your data security.
Frequently asked questions
What is the difference between network DLP and endpoint DLP?
Network DLP scrutinizes data in motion across routers and gateways, while endpoint DLP controls data at rest or in use on servers, laptops, and mobile devices. Both complement each other for full-lifecycle coverage.
Does network DLP slow down traffic?
Modern appliances use hardware acceleration and artificial intelligence to inspect packets at line rate. With proper sizing, latency remains negligible.
Can network DLP work in encrypted environments?
Yes. Policies can enforce TLS decryption at trusted proxies or rely on metadata analysis and cloud API inspection when decrypting traffic is impossible.




