What keeps your fleet running, connected tech, is now exactly what makes it vulnerable to cybercriminals.
ELDs, telematics, and routing software keep operations moving, creating new vulnerabilities. In Q3 2024 alone, cargo theft jumped 14%, with over $39 million in stolen freight. And that’s just the physical side; ransomware, phishing, and system takeovers are hitting fleets hard.
When one cyberattack can stall trucks, freeze dispatch, and leak sensitive data, cybersecurity stops being an IT issue, it becomes a survival strategy.
This article breaks down the most significant cyber threats facing today’s trucking companies and gives you clear, practical steps to protect your fleet and bottom line before attackers strike.
Key Takeaways
- Connected tech is fueling a rise in cyberattacks across the trucking industry.
- Ransomware and phishing are the top threats targeting fleets.
- Small fleets face bigger risks with fewer defenses.
- Smart protection starts with audits, MFA, training, and backups.
- Cybersecurity experts help keep your fleet secure and moving.
Why Cybersecurity Matters in Trucking
Cyberattacks threaten the trucking industry, disrupting day-to-day operations and exposing transportation companies to serious financial and legal repercussions.
When hackers infiltrate on-board systems or telematics, they can trigger operational downtime, manipulate routing data, or even cause safety hazards for truckers on the road. Beyond lost revenue, a successful breach often results in stolen sensitive information like driver credentials, cargo details, and corporate data, threatening a company’s reputation and client trust.
Vulnerabilities expand as vehicles rely more on autonomous driving features and advanced analytics. Malicious actors may exploit unpatched software or compromised APIs to gain unauthorized access, exposing small business fleets and large motor carriers to potential data breach incidents. For instance, a single ransomware attack can grind an entire fleet to a halt, bringing massive recovery costs and long-term damage to brand image.
In this environment, protecting sensitive data is paramount. Strong cybersecurity keeps criminals out, helps you meet regulations, and protects customer trust. From securing the supply chain to safeguarding real-time tracking systems, trucking companies cannot afford to overlook cybersecurity. Every connected device, from an ELD to a dispatch server, represents a potential entry point for bad actors.
Common Cyber Threats Faced by Trucking Fleets
Ransomware is one of the biggest threats to fleets today. Hackers lock down critical files and demand payment to restore access, stall deliveries, disrupt the supply chain, and rack up serious costs.
Phishing is another top danger. A single fake email from a “trusted” contact can lead to data theft, system hijacking, or even rerouted freight.
Then there’s unauthorized access, which is usually caused by weak passwords or poorly secured admin accounts. Smaller fleets are at risk without strong IT support or regular employee training.
According to NMFTA, basic protections like password policies and response plans can reduce exposure. Knowing these common threats is the first step. Acting on them protects your data, keeps your trucks moving, and avoids costly downtime.
Best Practices for Cybersecurity in Trucking
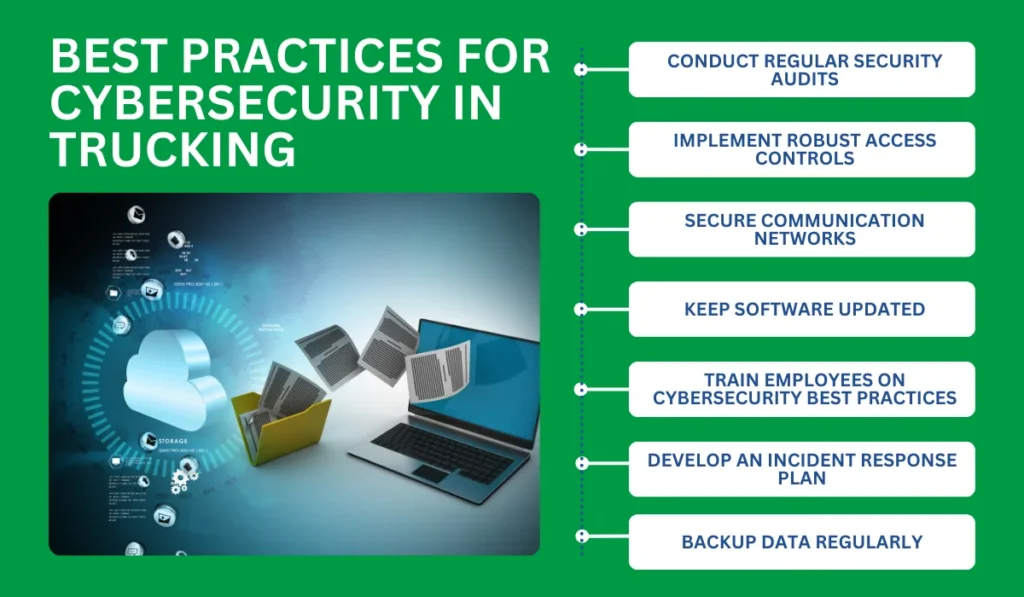
1. Conduct Regular Security Audits
Staying ahead of cyberattacks begins with frequent security audits to discover hidden vulnerabilities. Tools like penetration testing and network scanning help identify weak entry points, while thorough reviews of telematics integrations and APIs ensure that data flows remain secure.
Consulting cybersecurity professionals or specialized trucking industry experts can provide an in-depth analysis tailored to your fleet. The National Motor Freight Traffic Association (NMFTA) also offers resources for motor carriers to benchmark their security posture.
2. Implement Robust Access Controls
Limiting who can access critical systems is essential for effective mitigation. Role-based access control (RBAC) restricts permissions to the bare minimum required, reducing the risk of unauthorized access.
Multi-factor authentication adds an extra layer of defense against phishing or password scams, lowering the chance of a data breach. For instance, requiring a token or mobile app confirmation can stop hackers from gaining entry even if passwords are compromised.
3. Secure Communication Networks
As more trucking companies use advanced fleet management systems, securing communication channels becomes critical.
Encrypting data transfers via virtual private networks (VPNs) or TLS protocols helps protect sensitive information from prying eyes. Because logistics companies often deal with cross-border transportation, ensuring end-to-end encryption for all devices in your fleet is vital.
4. Keep Software Updated
Outdated software is one of the most common cybersecurity threats. Regularly installing patches or updates closes potential exploits that hackers eagerly look for. Whether it’s an ELD or dispatch system, scheduling frequent updates across all connected devices can reduce vulnerabilities.
Remember to verify compatibility between systems, especially when dealing with third-party APIs.
5. Train Employees on Cybersecurity Best Practices
Human error remains a top cause of cyber risks. Ongoing cybersecurity training ensures employees can spot phishing attacks, recognize suspicious activity, and report anomalies. Train your team on strong password habits and why sharing credentials is a no-go.
By following NMFTA guidelines and other recognized frameworks, you reinforce a culture of cyber awareness.
6. Develop an Incident Response Plan
A well-documented incident response plan outlines how to contain and investigate any cybersecurity attack. The plan should include steps for quick operation restoration, forensic analysis, and communication with relevant stakeholders. Rapid response is vital to minimize downtime and protect your reputation.
7. Backup Data Regularly
Regular backups offer peace of mind if a ransomware attack or data breach occurs. Consider both on-site and cloud-based solutions for redundancy. Testing these backups periodically is just as important; restoring from unverified backups can lead to further complications.
Cybersecurity isn’t one-size-fits-all. Tailor your defenses to fit your fleet’s size and budget.
Tailored Solutions for Small and Mid-Sized Fleets
Cybersecurity can feel out of reach if you run a smaller fleet, but it doesn’t have to be. Limited budgets and lean IT teams are common, but affordable protection is possible.
Start with the basics: low-cost firewalls, trusted antivirus tools, and free training resources from the NMFTA. These alone can help you spot and close key vulnerabilities, no full-scale IT department needed.
Partnering with reputable vendors can also level the playing field. Many offer affordable tools for threat monitoring, patch management, and incident response tailored to small and mid-sized operations.
Focus your efforts where they matter most: employee training, multi-factor authentication, and regular software updates. These low-cost moves pack a big punch, and when tailored to your fleet’s size, they go a long way toward keeping cybercriminals out and your trucks on the road.
Partnering with Cybersecurity Experts
Collaborating with cybersecurity experts who understand the transportation industry is a strategic move for trucking companies. These specialized cybersecurity professionals offer real-time monitoring, advanced intrusion detection systems (IDPS), and comprehensive incident response plans that adapt to your fleet’s evolving needs. They also deliver tailored cybersecurity training for employees, minimizing entry points for hackers.
Whether you operate a single truck or an entire fleet across North America, expert guidance ensures your security measures stay up-to-date. From risk assessments to disaster recovery planning, working with knowledgeable partners can significantly reduce disruptions and maintain compliance with industry standards, ultimately safeguarding your bottom line.
Conclusion
One breach can stop your fleet cold.
Whether you manage 10 trucks or 1,000, your operation depends on secure, uninterrupted tech. And when the next cyber threat hits, and it will, your preparation will be the difference between a minor hiccup and a full-blown crisis.
Keystone Technology Consultants specializes in cybersecurity for trucking companies, offering real-time monitoring, incident response planning, and IT strategies built for the road.
Don’t wait until a breach parks your fleet. Partner with Keystone Technology Consultants to secure your fleet and keep your operations moving forward.




