Cyberattacks aren’t just increasing; they’re evolving faster than many organizations can manage. You’re already behind if you’re still relying on scattered tools and reactive measures. Real protection begins with a cohesive IT security architecture that embeds data protection, authentication, and infrastructure design at the core of your operations.
The stakes are even higher for manufacturers and other high-risk sectors. A Deloitte study found that only 29% of manufacturing companies have implemented effective cybersecurity measures. That gap isn’t just a compliance issue; it’s a business risk. Sensitive data, application security, Virtual Private Network (VPN) configurations, and even endpoint devices are all potential points of failure without a strong architecture in place.
This guide is designed for forward-thinking security architects, Chief Information Security Officers (CISOs), and stakeholders who know that ad-hoc security systems aren’t enough. We’ll walk you through proven cybersecurity frameworks, address industry standards, and offer practical, actionable strategies to reduce malware exposure, prevent data loss, and strengthen your security posture from the inside out.
Key Takeaways
- Embed Security Early, Avoid Expensive Surprises: Stop reacting to breaches; embed security into your IT planning early to reduce vulnerabilities and avoid costly fixes.
- Align Cybersecurity with Business Objectives: Use frameworks like SABSA and TOGAF to connect cybersecurity directly to your strategic goals, demonstrating measurable business value beyond compliance.
- Prioritize Zero Trust and Least Privilege: Immediately evaluate your current access controls and adopt Zero Trust and least-privilege models to minimize internal threats and data exposure risks significantly.
- Automate to Optimize: Implement automated tools for threat detection, patch management, and incident response to reduce human error, freeing your security team to focus on strategic threats.
- Consistent Training Closes Security Gaps: Provide regular, targeted cybersecurity training, especially in vulnerable sectors like manufacturing, to reduce human error, the top cause of breaches.
What is IT Security Architecture?
IT security architecture defines how your organization protects its information assets through a structured design. It ensures confidentiality, integrity, and availability across all technology layers, aligning closely with business goals.
Key objectives include:
- Risk management: Identifying, assessing, and mitigating security risks.
- Strategic alignment: Aligning security efforts with business objectives.
- Standardization: Promoting consistent security policies and technologies.
- Resilience: Building agile systems capable of adapting to emerging cyber threats.
- Compliance: Ensuring adherence to regulatory standards such as the General Data Protection Regulation (GDPR), the Health Insurance Portability and Accountability Act (HIPAA), and the International Organization for Standardization (ISO) standard 27001.
Unlike incident response, which reacts after breaches occur, security architecture helps stop threats before they happen. Security policies define what to protect, while security architecture shows how to do it. It involves policies, processes, people, and technologies, creating a cohesive cybersecurity ecosystem.
Why a Strong IT Security Architecture is Indispensable
Security is a living strategy that must evolve with your business and the threat landscape. A strong IT security architecture provides more than technical protection. It empowers decision-makers, aligns cybersecurity with core business functions, and builds the foundation for long-term success.
A robust IT security architecture provides numerous strategic advantages:
1. Proactive risk mitigation: Security architecture identifies vulnerabilities early, preventing cyber threats before they cause harm. Prevention is crucial, with the average cost of data breaches reaching $4.88 million according to IBM.
2. Enhanced defense-in-depth: Layered security controls, from network security and firewalls to endpoint protection, ensure that if one layer fails, others protect sensitive information.
3. Optimized security investments: Strategic architecture prevents redundancy, ensuring cybersecurity spending is focused effectively and efficiently.
4. Seamless compliance & governance: A structured security framework simplifies meeting compliance standards (e.g., ISO 27001, GDPR), reducing audit complexity and compliance risk.
5. Supports digital innovation: Secure foundations enable the adoption of technologies like cloud services and IoT without compromising security, fostering innovation safely.
6. Improved operational efficiency: Architecture streamlines security operations through automation, reducing security issues and downtime.
7. Better business continuity: Systems with robust security measures can quickly recover from security incidents, minimizing disruptions.
8. Clearer accountability: Defined roles and responsibilities strengthen organizational cybersecurity culture and accountability.
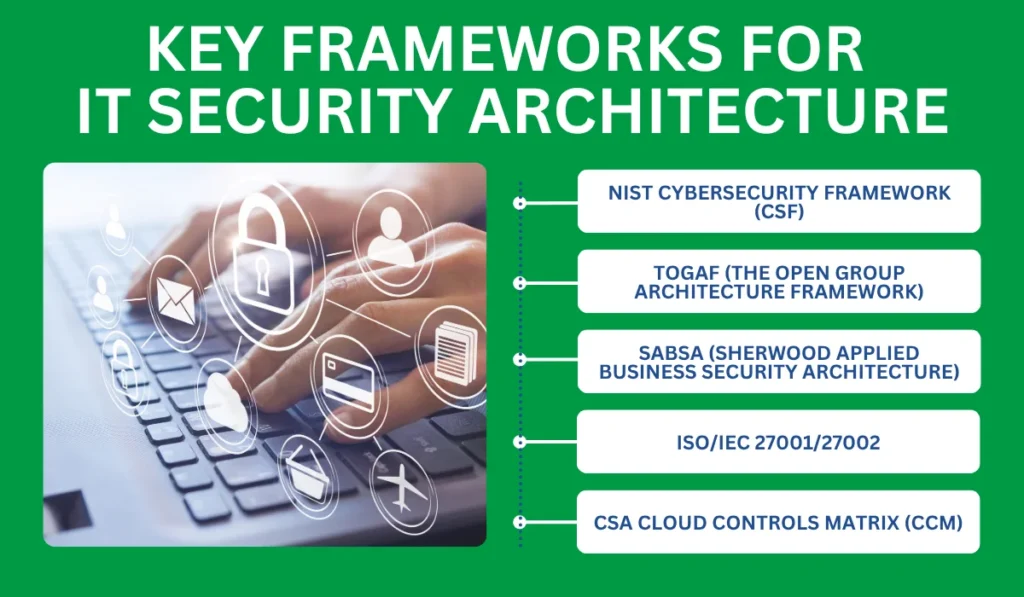
Key Frameworks for IT Security Architecture
Frameworks provide proven, repeatable models to help organizations make informed security decisions. Without structure, even the best security tools fail; misalignment and inconsistency undermine everything.
The frameworks below are widely respected across industries, provide practical, scalable guidance, and comply with regulatory requirements.
1. NIST Cybersecurity Framework (CSF)
The National Institute of Standards and Technology (NIST) CSF provides a voluntary, adaptive framework for managing cybersecurity risk. It defines five core functions:
- Identify
- Protect
- Detect
- Respond
- Recover
It helps you assess your security posture, find gaps, and create a roadmap aligned with cybersecurity standards.
2. TOGAF (The Open Group Architecture Framework)
TOGAF is an enterprise architecture methodology that includes robust security guidelines. Its Architecture Development Method (ADM) ensures security architecture aligns with broader business strategies, promoting consistency and standardization.
3. SABSA (Sherwood Applied Business Security Architecture)
SABSA defines security from the perspective of business objectives, translating these into technical requirements. It consists of six layers: Contextual, Conceptual, Logical, Physical, Component, and Operational. This ensures security aligns directly with organizational goals and risk management.
4. ISO/IEC 27001/27002
ISO 27001 sets standards for implementing an Information Security Management System (ISMS), while IEC (International Electrotechnical Commission) 27002 outlines best-practice security controls. Adopting ISO standards helps organizations build structured, comprehensive security policies essential for effective cybersecurity management.
5. CSA Cloud Controls Matrix (CCM)
The Cloud Security Alliance Cloud Controls Matrix (CCM) addresses cloud-specific cybersecurity concerns across IaaS, PaaS, and SaaS environments. Adopting this framework ensures cloud security compliance and best practices, which are essential as businesses increasingly rely on cloud infrastructure.
Best Practices in IT Security Architecture
To build an effective security architecture, implement these best practices:
1. Business-driven approach: Align cybersecurity efforts with organizational objectives, compliance requirements, and risk tolerance, ensuring security supports strategic goals.
2. Defense-in-depth: Multiple protective layers, network security, firewalls, intrusion detection, endpoint security, and more, ensure that no single security failure compromises the entire system.
3. Principle of least privilege: Grant users only necessary permissions. This minimizes damage if unauthorized access occurs and limits potential threats.
4. Zero-trust architecture: Adopt a “never trust, always verify” mindset. Continuous identity checks reduce insider threats and limit attacker movement.
5. Automation and orchestration: Automating repetitive cybersecurity tasks reduces human error, enhances efficiency, and enables rapid responses to security breaches.
6. Security by design/default: Use DevSecOps to build security from the start; don’t retrofit it later.
7. Continuous monitoring: Regularly assess security posture using real-time monitoring, incident response, and threat intelligence to adapt swiftly to evolving threats.
8. Threat modeling: Systematically analyze potential vulnerabilities and threats during the early design stages, proactively addressing risks before exploitation.
9. Centralized security management: Employ integrated platforms like Security Information and Event Management (SIEM) and Security Orchestration, Automation, and Response (SOAR) to streamline cybersecurity operations and provide comprehensive visibility and control.
Phases of IT Security Architecture Implementation
You don’t build security architecture in a day. It’s an iterative process that must evolve with the organization’s risk profile, technology stack, and regulatory environment. These implementation phases help break down the complexity and ensure your architecture is built on a firm, adaptable foundation.
Effective security architecture involves a structured lifecycle:
1. Assessment & Discovery
Conduct risk assessments, identify critical IT assets, and evaluate current security policies and infrastructure. This phase reveals security gaps and business-specific cybersecurity requirements.
2. Design & Planning
Select appropriate security frameworks, outline security requirements, and develop conceptual and logical security architectures. This stage produces a clear security blueprint, technology recommendations, and a strategic implementation roadmap.
3. Implementation & Integration
Deploy and integrate selected cybersecurity solutions, such as IAM (identity and access management), firewalls, endpoint protection, and SIEM. This phase results in operational security measures and updated security policies.
4. Validation & Testing
Perform penetration testing, vulnerability assessments, and audits to ensure security effectiveness. This helps identify remaining vulnerabilities and refine response protocols.
5. Operations & Continuous Improvement
Regular monitoring, incident response, and security audits ensure ongoing cybersecurity resilience. This continuous improvement phase adapts to new threats, ensuring enduring protection.
Keystone: Your Partner in Building Robust IT Security Architecture
Designing and maintaining effective security architecture is a business-critical initiative that demands deep expertise, cross-functional alignment, and a forward-looking strategy. Keystone helps you turn complex cybersecurity needs into clear, scalable outcomes with confidence and execution.
We deliver end-to-end security services purpose-built for organizations serious about resilience:
- Strategic advisory: Navigate frameworks, regulations, and business priorities with confidence.
- Risk and gap analysis: Uncover and address your most critical vulnerabilities before attackers do.
- Solution implementation: Deploy layered cybersecurity defenses across your network, endpoints, and applications.
- Policy development: Establish clear, enforceable cybersecurity policies aligned to your business needs.
- Continuous optimization: Keep your security architecture agile and adaptive in the face of evolving threats.
When you partner with Keystone, you’re not just checking a compliance box. You’re investing in a security strategy that protects your most valuable assets, earns stakeholder trust, and empowers your business to grow securely.
Ready to turn cybersecurity into a strategic advantage? Contact Keystone today to build a security architecture that protects today and prepares you for tomorrow.
Conclusion
Patchwork security tools and outdated protocols won’t withstand today’s sophisticated cyber threats. True protection comes from a unified strategy that weaves IT security architecture into every layer of your operations. It strengthens your entire digital environment, from data protection and authentication to application security and access control.
Your organization deserves more than temporary fixes. It needs future-proof security solutions that align with its business goals, reduce risk exposure, and support digital innovation. Implementing the right frameworks, leveraging best practices, and working with the right security architects can build a proactive, agile, and resilient cybersecurity posture.
Keystone delivers enterprise-grade security services designed to protect what matters most. Our tailored security solutions help you stay ahead of evolving threats, maintain compliance, and confidently operate.
Now is the time to stop reacting and start leading. Contact Keystone today to schedule your strategy session and discover how our IT security architecture services can transform your cybersecurity from a weak point into your strongest asset.




